
The big fear in the escrow industry is FRAUD. It always has been. Identity fraud, check fraud, and wire fraud has always been a risk for any company that holds other people’s money in an escrow trust account.
What has been alarming in recent years is how fraudsters have become much more clever and sophisticated to try to score that big hit. The introduction of newer technologies has led to that increased risk, mostly because consumers are less aware of how said technologies work and how to protect themselves while using it. This article will examine the first of those new technologies… Email.
Email is a major gateway to fraud!
Email deserves a special distinction for being the first technology that we use to identify other people without using our basic senses. When we receive an email from a person, we are only loosely identifying that person because of the email address. We don’t see the person’s face, and we don’t hear the person’s voice. It’s second-hand identification that is treated like primary identification because of the convenience of its use. What are the pitfalls that occur when we rely on this loose identification?
- What if the email address is fake?
- What if someone hacks into their email address and impersonates them?
- What if someone hacks into MY email address and impersonates me?
Going by the above, e-mail fraud can be summed up as identity fraud in the information era. What can we do about it? There are 2 ways to go about reducing your risk of email fraud:
- Proper e-mail and web browsing habits to address the first 2 bullet points above
- Maintaining strong email security to address the 3rd bullet point above
Be diligent and hover over email addresses and links before proceeding
The term for impersonating someone else via fake emails is called phishing. The simplest element to understand about phishing is that the person’s name that appears on the “From” line, heading, or signature does not properly identify them. The only way to identify someone from their email address is to hover over their email address and read what it says. If it is correct, great, you will have passed step 1 (but you are not done yet, see further steps below). If it is not… well, time to ignore it and/or alert that particular person separately.
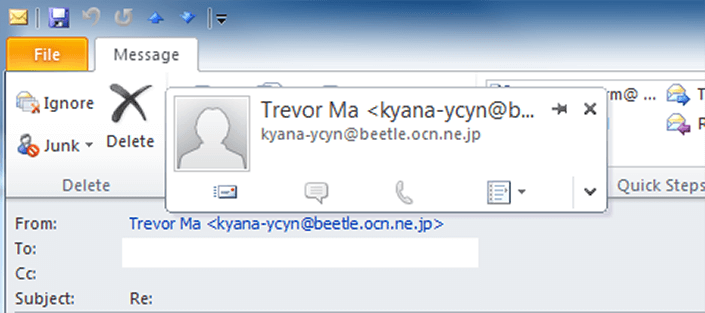
The above is a snippet of a spam email that is trying to impersonate me. With whatever email program or app you use, you can and should see beyond the name and check the email address. This can be done by hovering over the name in the “From” field (see the above picture) which shows the name they are trying to impersonate and the actual email address below it.
Also, beware of misspellings in the email address. Phishers will try to trick you by registering an email address as close to the original as possible. This is especially a risk with popular services like Gmail or Yahoo. Juliiana@gmail is definitely not Juliana@gmail. Please, slow down and take the extra second to double check your sender email addresses before you open that email. Make sure you know how to do this with whatever program or app you use for your email.
Do not automatically assume everything is fine just because the email address is correct
Ok, so you checked the actual email address and it is correct. That means this message is really from your client and anything they say or request of you is also fine, right? Well, of course not. Once again, you can’t verify anything about the person who typed the email message.
What if your client left their email program open and went to use the restroom and someone else snuck on really quick to type this message?
What if they used a public workstation and forgot to log out of their email after they were done?
What if your client’s email got hacked into and they haven’t realized it or haven’t told you separately?
There are a myriad of possible scenarios where the sender is a fake. Those are things you cannot control, but what you can control is how you conduct your internet and email practices.
Slow down when it comes to email communication.
While it varies between companies and industries, the culture around work emails tends to be: if you are at your computer and a work email comes in, you should take care of it right away. This is one of the biggest risk factors when doing business by email – everything is rush rush rush and get it done.
A common cited example is that you have arranged an escrow closing and everything is about to be completed when you suddenly get an email from your seller. The seller is asking if you can wire their net proceeds to their other bank account, different from what their initial wire instructions from the start of escrow were. They are also telling you to rush it as they are going on vacation tonight and want their confirmation and peace of mind. Talk about going into a cold sweat! Slow down and question it!
Fraudsters will often push forward a sense of urgency to try to coerce you into action without you analyzing the situation or they make you skip critical steps in your operating procedure. Any change with regards to funds disbursement should be a red flag and should alert you to slow things down for the safety of both yourself and your clients. There is no mistake in escrow more terrifying than sending a wire to the wrong account. Again, slow down and question it! Next…
Verify the information independently.
If you think an email message is suspicious or being faked, you should rightfully be suspicious of anything that is within that email message. That includes website links, mailing addresses, and phone numbers. If they are phishing or have hacked into that email address, it seems obvious they will alter everything within that email message to point to their fake websites and fake representatives to scam you.
Do not try to follow up by using anything within that email message. If the email sender is a bank or business, go to them separately by looking them up yourself on Google and see if the information matches. See if there are any search links that happen to ask if the particular company or message is a scam. If you are suspicious about an individual’s email message, use the phone number that you got from your first physical contact with them, not what’s written in the email.
Finally, if you cannot completely verify the information independently, hold off on their request until you can. Fraud prevention should always be adopting a “better safe than sorry” attitude.
What happens if my email gets hacked into?
You do all you can to be aware of how others might trick you. But what if “you” are the trickster yourself? How would you even know?
If fraudsters are impersonating you, you cannot track the emails they send out unless someone else informs you saying there is a faker pretending to be you. If fraudsters have gained access to your actual emails or email address, you don’t necessarily know either. That’s because if they send out an email under your real email address, they can also delete the Sent email from your own records or potentially mask it some other way.
There are 2 things that tend to happen if someone’s email address actually gets broken into.
1. Your password is changed and the fraudster has blocked access to your email. This might be to make a quick grab-and-go of whatever is in your email. However, this blockage is usually temporary as phone text recovery or a secondary recovery email address are options for the normal user. For businesses with their own email server, the administrator can perform recovery. The one solace in this scenario is that you immediately know you were broken into and can begin steps to recover and prevent it from happening again.
2. The fraudster knows your password and is discreetly spying on your email. This is by far the more terrifying scenario. They will monitor your emails via 2 methods – by logging in periodically and/or by setting a forwarding address to have your email activity remotely monitored at their location. This is usually how fraudsters inject themselves into a legitimate real estate transaction at the opportune time. As the escrow is preparing to close, the principals and agents are often exchanging status updates so an outsider reading these emails can observe the timeline of events. The fraudster, depending on whose email they have infiltrated, can masquerade at the right time to deliver fake wire instructions, get the money and quickly disappear by the time the error is noticed.
Do the following and more if your email was broken into:
1. Immediately let your IT administrator and your superior know. Time is of the essence with regards to email fraud and they can help with securing your email address and contacting the proper authorities and cybercrime units.
2. Change your password if you have access to the email account. When you discover your email has been broken into, you usually do not know how it occurred or for how long the breach has existed. Be sure you use a completely unique password.
3. Take stock of what is in your email address and what information might have been stolen. This includes your Contact list, Notes, and email chains along with attachments. Within an escrow transaction, clients or agents will often send personal information or documents via email as requested by the escrow company or lender. Non public personal information (NPPI) such as Statement of Information sheets, 1003 loan applications, or copies of mortgage statements, are at risk of being stolen or getting leaked out. Seek out your legal counsel for questions regarding notifying affected parties.
4. You or your IT administrator should also run a virus and malware scan on your computer. Sometimes, fraudsters get your email password through malware that analyzes what you type. This is called a keylogger. Going to an unsafe website via fake or phished emails can also cause malware to be installed on your computer. And if you ever entered a username and password on a fake website, that password is no longer safe or usable.
5. Check your email settings to see if there are any unusual changes. These can include forwarding addresses that are not familiar to you, as well as white-listed email addresses (email addresses that your account will not block), or routing information. Pretty much any foreign email address or server that appears within your email settings needs to be scrutinized; refer anything unfamiliar to your IT administrator. Take note of these settings (taking a picture with a smartphone camera is pretty helpful) before changing or removing them.
6. Gather email activity logs and notifications if possible. This can include unusual automated messages like “attempts to login at a new location or device” and “email undeliverable” messages. Information like this can help determine how long a breach was active and to where.
7. Be extra cautious of any changes in the future, both with email conversations and in your business transactions. You just realized you are vulnerable and have been vulnerable for a period of time. Fix the errors that have occurred and look to prevent any future loss. For a real estate transaction, that can mean taking extra precautions when sending wire funds and electronic documents.
Implement more email security if necessary
One of the more straightforward ways to protect yourself is to implement two-factor authentication (2FA) for your email address. Anything with 2FA requires two steps to traditionally log in: a password and a second more local key. This key can either be a text message sent to your phone, a code from a linked token device, or a fingerprint or retina scanner. 2FA dramatically increases the difficulty of breaking into something because the 2nd factor is a local unique item that the fraudster must have not only for this time, but also every time they want to break in.
The tradeoff as with all things security related, is the reduction in convenience as you have to take extra steps and potentially carry an extra item with you. However, for many high tech industries whose livelihood is in intellectual property or sensitive NPPI, two-factor authorization is just one of a handful of security implementations needed in today’s business world. Google and Yahoo emails also have 2FA as a feature for normal users.
Passwords! This section is really important!
Use a unique password for your email address that you do not use for anything else. It bears repeating that this is something you should be doing for all of your online sites, but especially for your email. This is because your email address is your digital home. Notifications, invoices, purchase receipts all go to your personal email address.
When someone gets access to such a trove of information, they now know the next online destinations of yours to break into. They now know which banks you use, part or all of your bank account numbers, your PayPal account, what purchases you made on Amazon, etc. If you used the same password for some of these other websites, you’ve given them even more to take away from you. So in that regard, do not transact personal business on your work email.
Compartmentalize your online activities, if only to reduce the headache of repairing any future damage. If you need to change your email password, do not re-use old passwords. Also, make sure you do this after you have scanned your computer for viruses so that there are no keyloggers tracking your new password.
To continue further with the analogy above, an email hacker is pretty much like a house burglar. They go for the easiest marks with the fewest protections. If your house has a strong alarm system, video cameras and you don’t leave the spare key in an easy to find spot, the burglar won’t bother with you and go somewhere else rather than take the time to crowbar and break your front door. Email security works the same way. Your password is your house key and if it is unique and unused anywhere else, the key is hard to find.
The worst thing you can do is use a password easily attributed to you or used on multiple sites, some of which may have already been compromised. It’s akin to just leaving your front door unlocked. Even if the hacker has your key, if you have 2FA, they still can’t get in and it acts like an alarm system. If you regularly sweep through your email and computer settings and run antivirus programs, these are looked on as your “video cameras” to track any wrongdoing that may have occurred.
Conclusion: It is a brave new world out there, try to keep up with changing technology
Email is great. It provides a written record of things stated and conversations that occurred. It allows multiple parties to be informed and instructions given out efficiently. But email also introduces hazards that previously did not exist with concerns to identity. Understanding how email fraud is perpetrated and practicing good internet habits are key to protecting yourself and your associates. Email fraud within the escrow industry is a mix of identity theft with wire fraud as the ultimate goal.
Take a minute and think about the above. Email is not even that new of a technology; the public has been using personal emails since the 1990s. It has been taken for granted, however, even as many facets of it are not adequately understood by the public.
What about newer technology?
How are you being tracked with your smartphone or your smartphone apps?
What may happen with personal microchips in the future?
What about other new technology that your business industry adopts (e-closings and remote online notarizations, for instance), not because your company wants to, but because your customers demand it?
Being aware of changes and new scams within technology (both new and old) is now a requirement to doing business while going about our daily tasks. Be safe, be aware, do your research, and take your time out there in the new digital era.

Trevor Ma
Office Manager
Trevor has been with Viva Escrow since 2010. He is on hand for all the daily tasks and challenges that occur within the office. As a result, he has picked up on a variety of topics for which he can write about to better serve our clients, our staff and our company needs.
