Trick or Treat Came Early
A Very Personal Ransomware Horror Story
As the IT person for Viva Escrow, I am in charge of keeping our technology secure and in place. This means not only hardware but also software. Unfortunately, my responsibilities have significantly increased in the past few years due to our incessant fear of systems failures, email compromise and possible loss of trust funds through wire fraud. My last article was about email fraud, which can be read at this link. That article delineated the signs of trouble and the necessity of conducting good internet practices. The intent was to convey the seriousness and scare the reader, but I have found that generalized articles like that do not really do the trick. The reader may shrug it off offhandedly and think, “This won’t happen to me.” How about I tell a more personal horror story?
We are a small, privately-owned company. A few years ago our company was hit with a system compromise and ransomware demand. This was even before ransomware became so “popular.” So let me tell you straightforwardly that, “Yes, it can happen, it is terrible and it could have ruined our business.”
What is ransomware? Ransomware is a particular type of computer virus that locks your files away and leaves a message stating you need to pay to have your files unlocked.
A number of health facilities and city government facilities were hit just in 2019. And these are just the ones we see on the news. There is no telling how many public and private companies, large or small, have been hit that we are not aware of. This type of fraud (and yes, it is the big bad word, FRAUD) has gained in popularity because the hacked entities are in distress, they pay, and it doesn’t take long for the perpetrators to realize that here is an effective way to make a lot of money illegally.
So here is my story.
At the end of a workday, one of our staff came to me and told me that something was wrong with her computer. Errors kept coming up on her escrow software, some functions of the software also did not work, and there was gibberish.

As I sat down at the computer, I confirmed that certain screens could not open and with a feeling of dread, I looked into the system file directory. To my horror, some of the files had been forcefully encrypted. My whole being froze over and for long seconds I went blank and all I could think was, “Oh, no. Oh, no.” And then the sweat began.
Think of it like this: you have a computer folder filled with pictures. Suddenly the pictures are renamed and completely converted into something barely resembling what it was before, unopenable and inoperable. This actually happened to her pictures folder, the Documents folder, the escrow software folder, and others. The only thing left uncorrupted was the Text document or HTML file at the top of the folder.
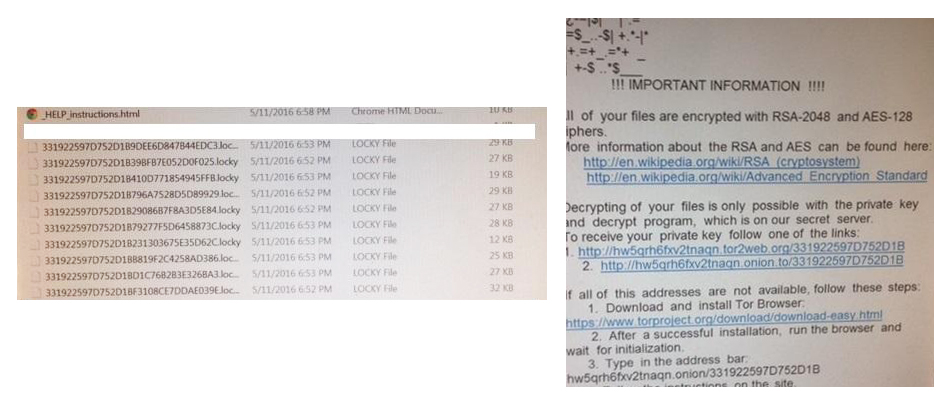
Written in the HTML document was the ransomware demand: “Your files are encrypted and go to the link below for further instructions.” No words could have expressed the sinking feeling in my stomach. I did not go further as I knew what our course of action was going to have to be. This was the reality of the situation:
- I cannot decrypt the files myself. It would be comparable to looking for a key without even knowing what the lock looks like. It would be impossible.
- Going to the provided link would not give me any assurance of recovering my files. The link would tell me the ransom demand and provide a bitcoin link to pay. What happens after? Do they take the payment and run or do they send me the decryption key? What if the key they send me is unsafe or contains some other hidden backdoor for them to infect us again?
- I had to make sure any traces of the ransomware or other virus were cleaned from that individual computer as well as the whole network. How many computer stations were affected? What about our network? I would have to immediately contact our IT consultant to make sure we swept through the system and secured our network.
- I then knew there was only one way to recover the now encrypted unusable files: pull up and re-install using our backup files. Fortunately, our company IT protocol had us performing daily tape backups as well as a comprehensive monthly backup. If we did not have the backups, the files that were encrypted and all that data would be lost forever.
So, how did the rest play out? Our saving grace was that our workstations were not made completely inoperable by this particular ransomware called Locky. Working in conjunction with our IT consultant, he checked our network and other servers while I worked on the directly infected computer. The antivirus software was able to scan through the computer and quarantine the remaining unsafe files. Luckily, only one computer station was infected and only a few of the network files. Once we determined we had removed all the infections, we restored the affected folders based on the backup tape. Regrettably, data entered between the last backup and the infection were permanently lost. The internal cleanup took hours and by the time this was all done, it was midnight. We had worked for 6 hours straight. The next morning, a call was made to the escrow software company and our network files were properly replaced.
Ransomware is scary because blackmail works
Why is ransomware a threat that needs to be given special consideration amongst other computer viruses and malware? Well, ransomware has a specific goal in mind: to get money through nefarious means. While other viruses may haphazardly just delete files or steal passwords and render computers inoperable, ransomware always hits you where it hurts the most: your data, your access to it, and your ability to conduct business. It is merciless in its ability to cripple you into submission so that you will pay up.

Going back to our experience with it, we put in six hours of work just to restore one single computer station that was affected. By good fortune and our strong existing network defenses, it did not spread rampantly through our network of 20 or so individual stations. Our other systems and drives did not need to be reformatted and all their programs reinstalled. Nevertheless, it was still painful and time-consuming. What if not only our escrow software failed, but other software or critical system programs failed? What if it had spread to every other computer station in the network and our servers? We would have been crippled for days or longer. We would not have been able to help our clients with their closing transactions. What if important client personal data had been accessed? In our community, our reputation would have been destroyed.
Is it Pay and Play?
Where would it get to the point that the least painful way to go would be to actually pay the ransom? In May 2019, ransomware crippled the city of Baltimore affecting their entire system and many municipal services. They were urged not to pay the $70,000 ransom by the FBI, which they didn’t. Since then the clean up has cost them $18 million so far. Would it have been worth it to pay? However, even if ransom was paid and the key given, they would still have needed to scrub and replace systems, but the alleviation of the short term pain might have been worth the cost of the ransom. Were I the decision-maker, even without knowing the future cost, even knowing the risk the decryption key would not fix the issues, I may have paid the ransom just so that at least some services could continue. It can be a desperate time and decisions made at that time may be good or bad. This is why ransomware is so successful and a major threat. Examples from other municipal cities: Riviera Beach in Florida was also a target and paid $600,000. On August 16, 2019, at least 22 cities in Texas were hit with ransomware demands. If you were in their IT department, what would you do?
Here is another serious consideration: What if replacing the computers and equipment is possible, but the backups were not sufficient or there were no backups at all? We would not have been able to access our client data and we would have been out of business for an indeterminate amount of time. At that point, paying the ransom would have been the only recourse as we would have been desperate to ascertain that our files would be freed. This is what the perpetrators are counting on. Whether it is our precious family photos, our thesis paper, the company personnel and financial files, customer data, customer non public personal information and files, or government records, at some point there is a price you would be willing to pay despite it being blackmail and a reward for nefarious acts.
What can you do to prepare against ransomware?
How did we get the ransomware? Ransomware is a computer virus and the vast majority of computer viruses begin their infection when the user of the computer opens an unsafe program or lets an unsafe script or macro run. The latter is probably what happened to us based on what we know about Locky. The worrisome part is that the user most likely did not even know what they did. One or two clicks in an unsafe site and the virus was planted. In essence, the user commits an action that causes infection to happen and often do not realize their action was unsafe. This is the challenge of IT departments worldwide, from small companies to large multinational corporations, hospitals and governments. Competent IT departments have a lot of underlying infrastructure in place to protect their networks, but that can only go so far. There must also be proper and continuous training for all users to ensure users don’t do something stupid or careless.

To summarize, it comes down to 3 very important things:
- Invest in anti-malware and anti-ransomware software. Make sure it is properly set up and running in the background of all your end-users. Good and up to date software can be that final secure wall to prevent the infection from taking effect. Be sure your systems are scanned frequently.
- Commit to awareness and training about ransomware and safe online practices. This tends to be more labor and time-intensive than setting up anti-malware software, but is arguably more important. If your users are being responsible with their online and network connections, the risk of infection for the present and the future goes down considerably. Teach them to be continuously aware of emails, attachments, and links.
- Maintain offline backups and back up frequently. This can include dedicated flash drives, tape backups, or disconnected hard drives. True backups should not be held on the same network as what they are backing up. The most destructive ransomware variants manage to corrupt backups that were held on the network itself. Store your backups somewhere safe and reliable so that they can be retrieved and usable in an emergency.
Victory and Defeat
With ransomware, bad guys get a victory but you mustn’t let this defeat control your business. Accept it and move forward.
There is a conception about the word ‘ransom’; that it is a failure on your part and that paying it makes you weak. It’s romanticized in movies with hostage situations in which good guys refuse to pay and action heroes swoop in to save the hostages and win the day. It gives the impression that paying ransom is always the wrong choice.
However, everyday life is not scripted and choices, whether good or not, must be made and accepted once made. Sometimes, paying that ransom is the choice that is made. From there, who and where does the blame get placed? To place the blame is useless but to review how the event happened is the learning lesson. You start at the root and go up:

- Does your system have malware protection? More importantly, is it an up-to-date newest version?
- Have you kept up with software company recommended patch requirements? Remember, hackers are continuously trying to hack into operating systems and notices to update your system should not be ignored. See this notice published by CNN
- Has your management put together continuous education for new and old staff? Do not let them forget to be aware of security issues every single time they go on the Internet or look at or click on an email link. You know the saying, “It takes a village.” In this case, it takes all members of the company to keep the company safe.
- What are your management procedures for worst case scenarios? Do you have a plan of action? Are you prepared to do what you need to if the virus attack happens?
The important thing is not the payment of ransom. What is important is how not to have to pay if it happens to you and how to get back up to speed with minimal disruption of service.
My company was lucky that the problem was isolated and solved relatively quickly. The worry-filled nights however, are continuous. Now that we have had a taste, prevention has become our present constant concern. From this defeat we have achieved a victory of sorts.
This article is for all of us, let us all be aware.
 Trevor Ma
Office ManagerTrevor has been with Viva Escrow since 2010. He is on hand for all the daily tasks and challenges that occur within the office. As a result, he has picked up on a variety of topics for which he can write about to better serve our clients, our staff and our company needs.
Trevor Ma
Office ManagerTrevor has been with Viva Escrow since 2010. He is on hand for all the daily tasks and challenges that occur within the office. As a result, he has picked up on a variety of topics for which he can write about to better serve our clients, our staff and our company needs.

